Microsoft warns of a evasive year-long spear-phishing campaign targeting Office 365 users
Security Affairs
AUGUST 12, 2021
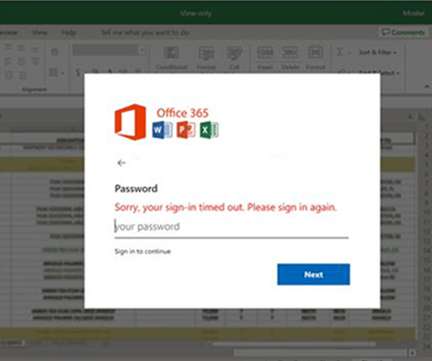
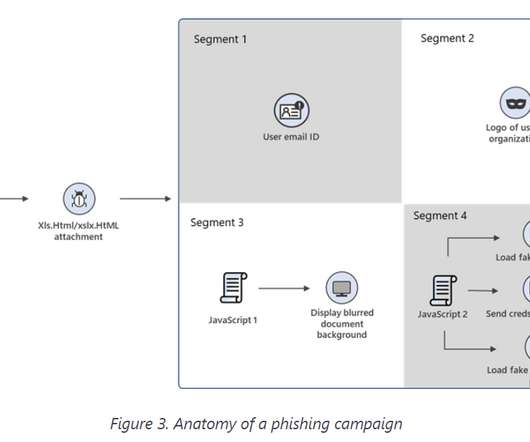
Microsoft warns of a long-running spear-phishing campaign that has targeted Office 365 customers in multiple attacks since July 2020. Microsoft revealed that a year-long spear-phishing campaign has targeted Office 365 customers in multiple attacks starting with July 2020. com , or api[.]statvoo[.]com












Let's personalize your content