UNC1945, a sophisticated threat actor used Oracle Solaris Zero-Day exploit
Security Affairs
NOVEMBER 3, 2020
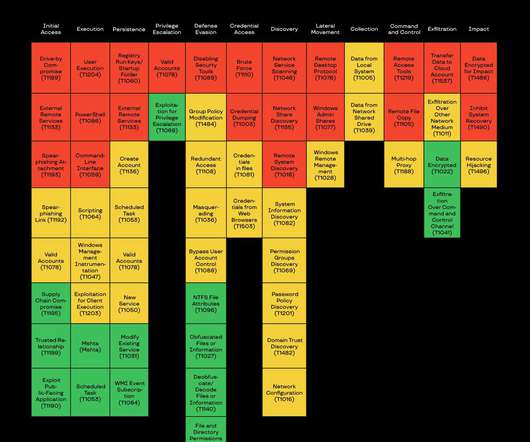
. “UNC1945 targeted Oracle Solaris operating systems, utilized several tools and utilities against Windows and Linux operating systems, loaded and operated custom virtual machines, and employed techniques to evade detection.” ” The attackers also used BlueKeep scanning tool to target Windows systems.













Let's personalize your content