Types of Cybersecurity Threats and Vulnerabilities
Security Boulevard
FEBRUARY 15, 2024
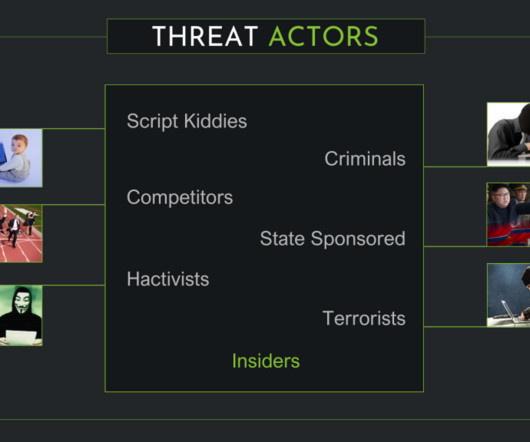
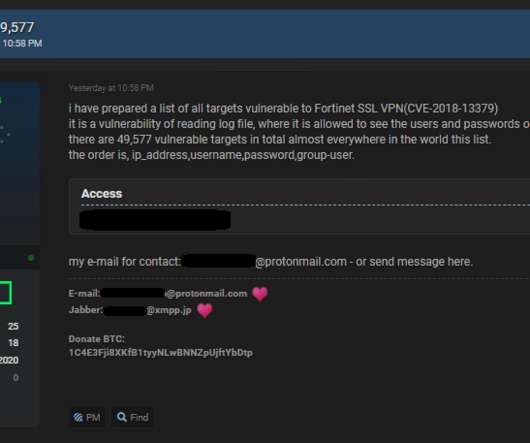
Reading Time: 4 min Uncover the types of cybersecurity threats and vulnerabilities lurking online! The post Types of Cybersecurity Threats and Vulnerabilities appeared first on Security Boulevard. Learn how to protect yourself with actionable tips and free resources. Stay safe online today!
















































Let's personalize your content