Mom’s Meals issues “Notice of Data Event”: What to know and what to do
Naked Security
AUGUST 29, 2023
It took six months for notifications to start, and we still don’t know exactly what went down… but here’s our advice on what to do.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.
Naked Security
AUGUST 29, 2023
It took six months for notifications to start, and we still don’t know exactly what went down… but here’s our advice on what to do.
Naked Security
JULY 31, 2023
When is a ransomware attack a reportable matter? And how long have you got to decide?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Naked Security
JULY 27, 2023
Fascinating fun (with a serious and educational side) – listen now! Full transcript available inside.
Naked Security
JULY 25, 2023
"You need to turn on a special setting to stop the code you wrote to stop the code you wrote to improve performance from reducing performance from reducing security.

Naked Security
JULY 24, 2023
Another month, another patch for in-the-wild iPhone malware (and a whole lot more).

Naked Security
JULY 24, 2023
“Three may keep a secret, if two of them are dead.

Naked Security
JULY 20, 2023
Latest episode – check it out now!

Naked Security
JUNE 29, 2023
Latest episode – listen now! (Full transcript inside.

Naked Security
JUNE 28, 2023
Technically, it’s “up to $10 million”, but it’s potentially a LOT of money, nevertheless…

Naked Security
JUNE 26, 2023
Not just that infamous Twitter hack, but SIM-swapping, stalking and swatting too…

Naked Security
JUNE 23, 2023
Don’t treat rebooting your phone once a day as a cybersecurity talisman… here are 8 additional tips for better mobile phone security.

Naked Security
JUNE 22, 2023
Lots to learn this week – listen now! (Full transcript inside.

Naked Security
JUNE 21, 2023
Apple didn’t use the words “Triangulation Trojan”, but you probably will.

Naked Security
JUNE 21, 2023
Did you prevent password-only logins on your SSH servers? On ALL of them? Are you sure about that?

Naked Security
JUNE 21, 2023
Get the full 360-degree view of ransomware

Naked Security
JUNE 20, 2023
“Do as we say, not as we do!” – The patches took ages to come out, but don’t let that lure you into taking ages to install them.

Naked Security
JUNE 19, 2023
One, sadly, has died, and two are heading to prison, but for Kim Dotcom, the saga goes on…

Naked Security
MAY 30, 2023
What good is a popup asking for your approval if an attacker can bypass it simply by suppressing it?

Naked Security
MAY 25, 2023
Latest episode - listen now. Full transcript inside.

Naked Security
MAY 24, 2023
Another traitorous sysadmin story, this one busted by system logs that gave his game away.

Naked Security
MAY 23, 2023
Controlled outage used to keep malware marauders from gumming up the works. Learn what you can do to help in future.
Naked Security
MAY 22, 2023
Site marketing video promised total anonymity, but that was a lie. 170 arrested already. Potentially 1000s more to follow.

Naked Security
MAY 4, 2023
Entertaining, educational, and all in plain English ??
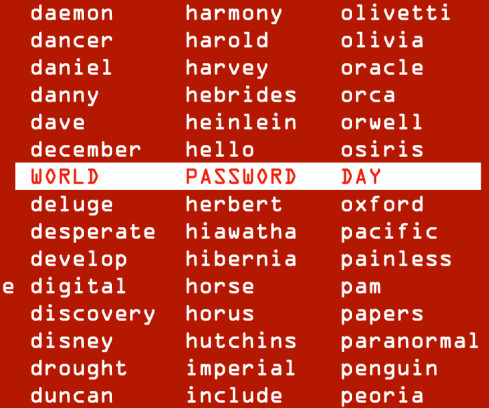
Naked Security
MAY 4, 2023
We've kept it short and simple, with no sermons, no judgmentalism, no tubthumping. and no BUY NOW buttons. Have a nice day!
Naked Security
MAY 3, 2023
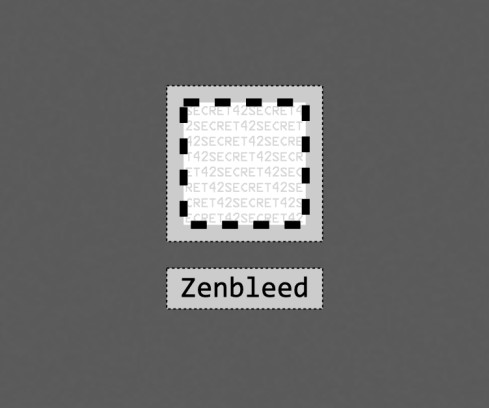
To bleat, or not to bleat, that is the question.

Naked Security
MAY 1, 2023
Just when we'd got used to three-numbered versions, such as "13.3.1", here comes an update suffix, bringing you "13.3.1 (a)".

Naked Security
APRIL 29, 2023
These malware peddlers are specifically going after Mac users. The hint's in the name: "Atomic macOS Stealer", or AMOS for short.

Naked Security
APRIL 28, 2023
CryptBot criminals are alleged to have plundered browser passwords, illicitly-snapped screenshots, cryptocurrency account data, and more.

Naked Security
APRIL 27, 2023
When Doug says, "Happy Remote Code Execution Day, Duck". it's irony.
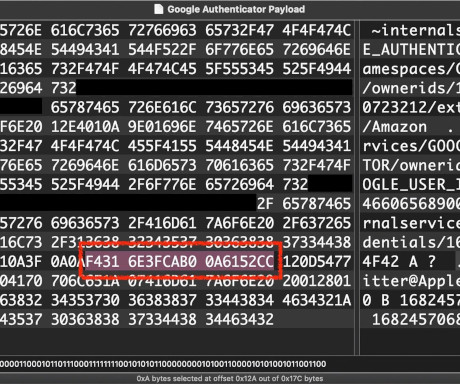
Naked Security
APRIL 26, 2023
You waited 13 years for this feature in Google Authenticator. Now researchers are advising you to wait a while longer, just in case.

Naked Security
APRIL 5, 2023
Grab a message/Play it back/You've just performed/A big phat hack.
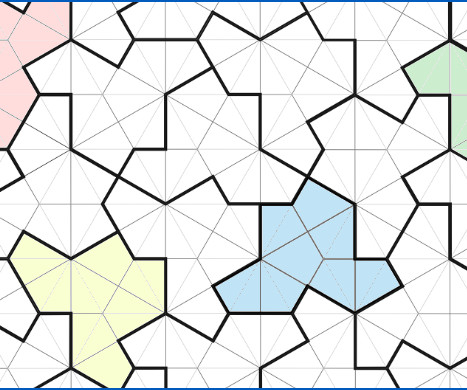
Naked Security
APRIL 4, 2023
Imagine tiling a whole football field using a single shape. yet not being able to produce a repeating pattern, even if you wanted to.

Naked Security
APRIL 3, 2023
They can't read much of your data, but even a few stray network packets could tell them something they're not supposed to know.

Naked Security
MARCH 30, 2023
The only backup you will ever regret is the one you didn't make.

Naked Security
MARCH 30, 2023
Latest episode - listen now!

Naked Security
MARCH 30, 2023
Booby-trapped app, apparently signed and shipped by 3CX itself after its source code repository was broken into.
Naked Security
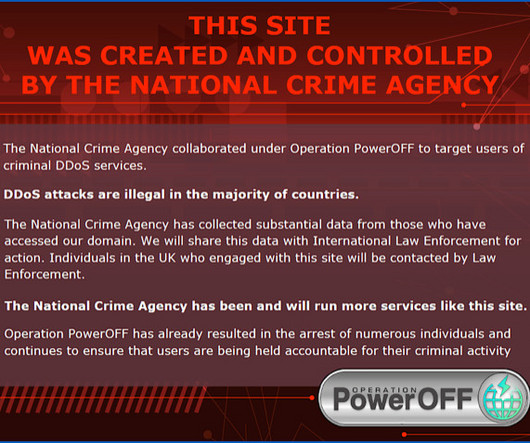
MARCH 28, 2023
Thinking of trying a bit of DDoSsing to get a feel for life at the fringes of the Dark Side? Don't do it!

Naked Security
MARCH 27, 2023
Got an older iPhone that can't run iOS 16? You've got a zero-day to deal with! That super-cool Studio Display monitor needs patching, too.
Naked Security
MARCH 27, 2023
Microsoft says "successful exploitation requires uncommon user interaction", but it's the innocent and accidental leakage of private data you should be concerned about.
Naked Security
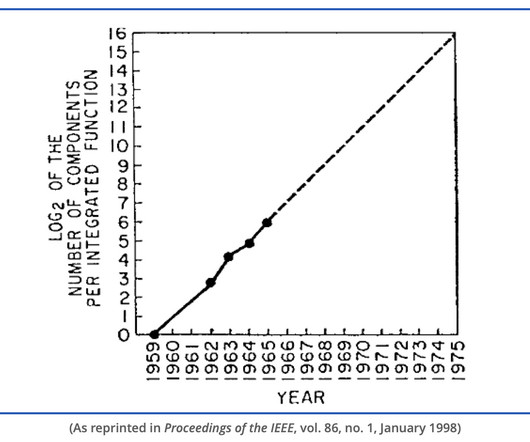
MARCH 26, 2023
His prediction was called a "Law", though it was an exhortation to engineering excellence as much it was an estimate.

Naked Security
MARCH 24, 2023
Admin-level holes in websites are always a bad thing. and for "bad", read "worse" if it's an e-commerce site.

Naked Security
MARCH 23, 2023
Listen now - latest episode. Full transcript inside.
Naked Security
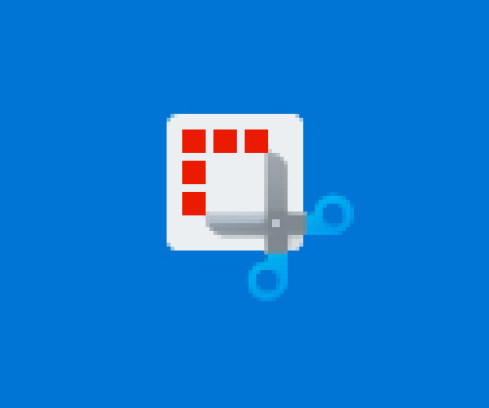
MARCH 22, 2023
Turns out that the Windows 11 Snipping Tool has the same "aCropalypse" data leakage bug as Pixel phones. Here's how to work around the problem.
Naked Security
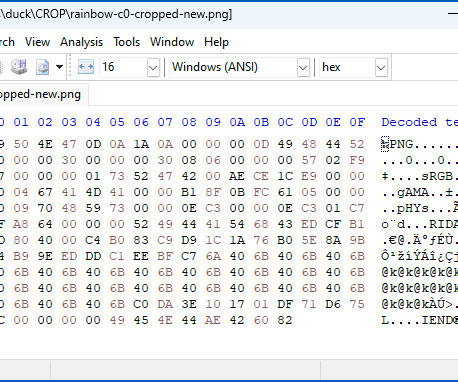
MARCH 21, 2023
What if the "safe" images you shared after carefully cropping them. had some or all of the "unsafe" pixels left behind anyway?
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content