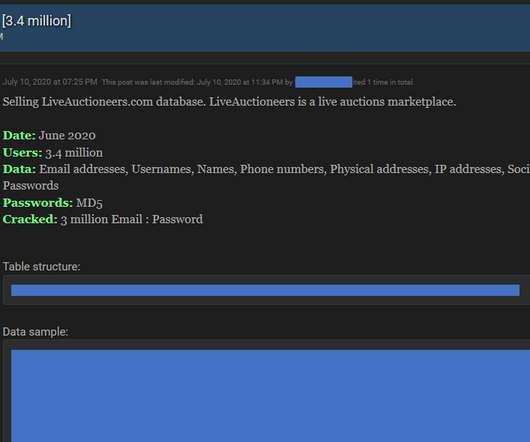
3.4 Million user records from LiveAuctioneers hack available for sale
Security Affairs
JULY 14, 2020
LiveAuctioneers is one of the world’s largest art, antiques & collectibles online marketplace that was founded in 2002. ” According to the company, attackers accessed personal details of the users, including names, email addresses, mailing addresses, phone numbers, and also encrypted passwords. million users.















Let's personalize your content