Spanish police dismantled SIM swapping gang who stole money from victims’ bank accounts
Security Affairs
FEBRUARY 10, 2022
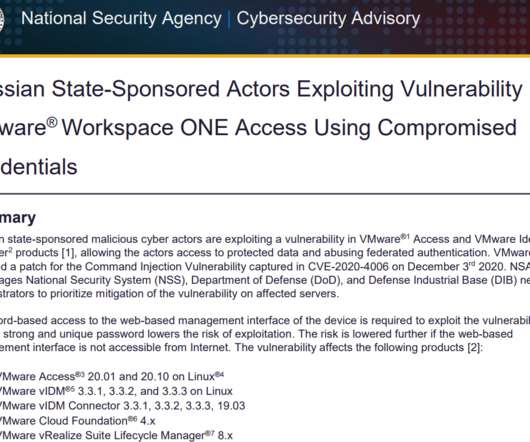
Spanish National Police has arrested eight alleged members of a crime organization who were able to steal money from the bank accounts of the victims through SIM swapping attacks. Once hijacked a SIM, the attackers can steal money, cryptocurrencies and personal information, including contacts synced with online accounts.

















Let's personalize your content