Financial cyberthreats in 2021
SecureList
FEBRUARY 23, 2022
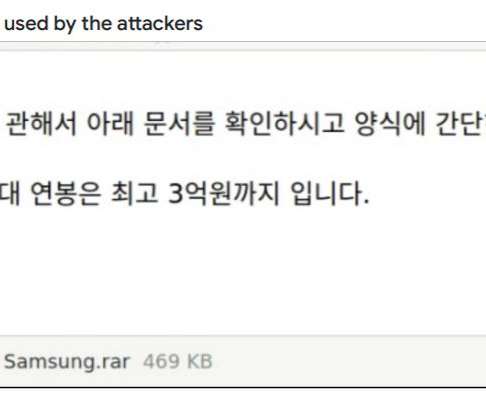
SpyEye, developed in 2009 and described as a “bank Trojan with a form grabbing capability”, surged from the eighth most common banking malware tool with a 3.4% Emotet (9.3%), described by Europol as “the world’s most dangerous malware”, underwent a drop of five percentage points between 2020 and 2021.This




























Let's personalize your content