Who and What is Behind the Malware Proxy Service SocksEscort?
Krebs on Security
JULY 25, 2023
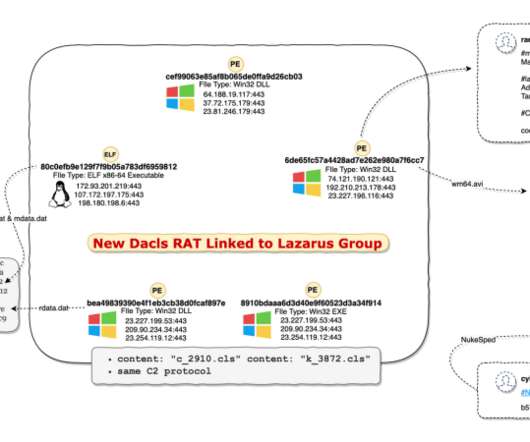
Now new findings reveal that AVrecon is the malware engine behind a 12-year-old service called SocksEscort , which rents hacked residential and small business devices to cybercriminals looking to hide their true location online. ” According to Kilmer, AVrecon is the malware that gives SocksEscort its proxies.
























Let's personalize your content