The History of Computer Viruses & Malware
eSecurity Planet
NOVEMBER 2, 2022
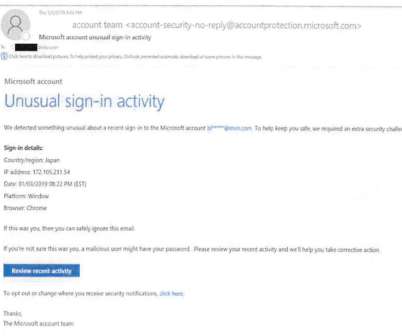
If you’ve used a computer for more than 5 minutes, you probably know a thing or two about computer viruses and malware. On the modern Internet, malware is a near-constant presence. Though often conflated with one another, malware and computer viruses aren’t necessarily the same thing. From Theory to Reality: 1948-1971.


























Let's personalize your content