Was 2013’s Target Security Breach Really Just The Work Of A Teenager?
SiteLock
AUGUST 27, 2021
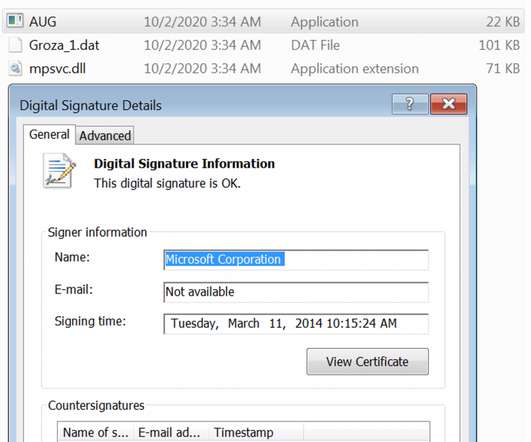
That’s exactly the news Target is dealing with, as security researchers suggest that at least one of the hackers behind the malware used to attack Target is barely 17 years old. Yet this teen was apparently able to develop a pretty sophisticated piece of malware, known as BlackPoS , that was used to infiltrate Target’s systems undetected.


































Let's personalize your content