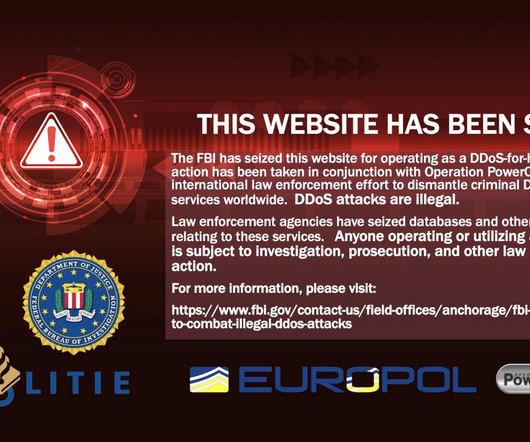
Law enforcement shutdown a long-standing DDoS-for-hire service
Security Affairs
JUNE 17, 2023
Polish police, as part of the international law enforcement operation PowerOFF, dismantled a DDoS-for-hire service that has been active since at least 2013. An international operation codenamed PowerOff led to the shutdown of a DDoS-for-hire service that has been active since at least 2013. Viewer discretion is advised.


















Let's personalize your content