Experts spotted a rare Linux Desktop spyware dubbed EvilGnome
Security Affairs
JULY 18, 2019
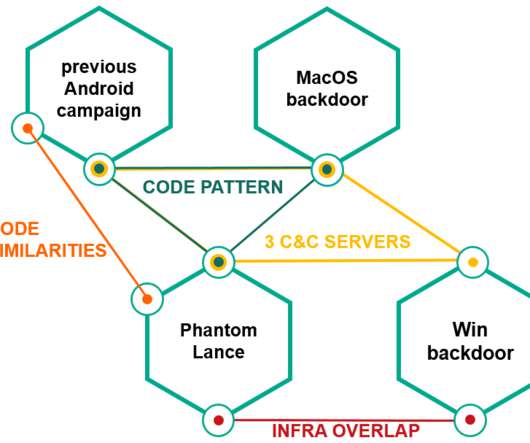
The researchers attribute the spyware to the Russia-linked and Gamaredon Group. The Gamaredon APT was first spotted in 2013, last year researchers at LookingGlass have shared the details of a cyber espionage campaign, tracked as Operation Armageddon , targeting Ukrainian entities. ” reads the analysis published by Intezer.















Let's personalize your content