Russian Cybercrime group is exploiting Zerologon flaw, Microsoft warns
Security Affairs
OCTOBER 10, 2020
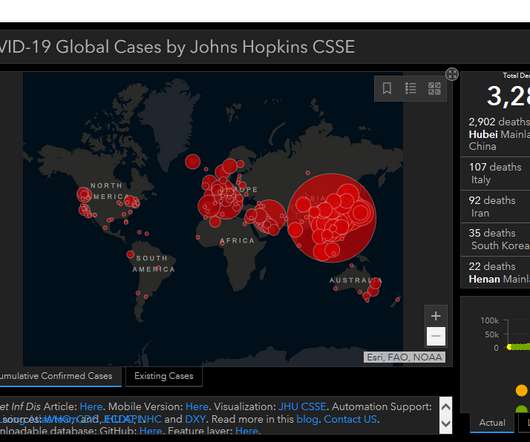
TA505 hacking group has been active since 2014 focusing on Retail and banking sectors. — Microsoft Security Intelligence (@MsftSecIntel) October 6, 2020. — Microsoft Security Intelligence (@MsftSecIntel) October 6, 2020. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->.






















Let's personalize your content