Microsoft warns TA505 changed tactic in an ongoing malware campaign
Security Affairs
FEBRUARY 2, 2020
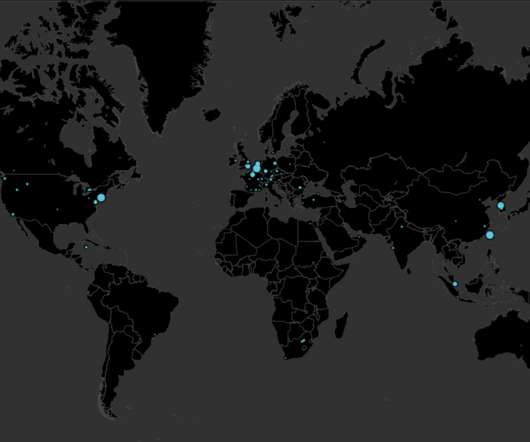
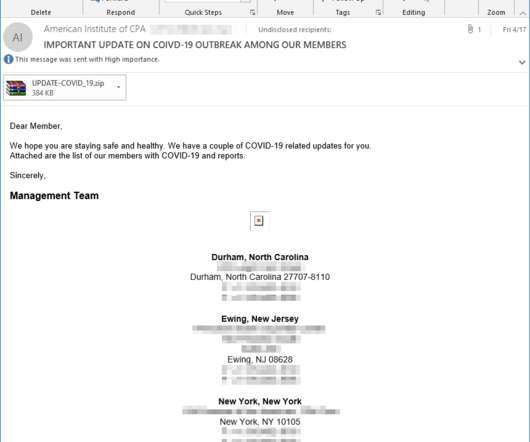
In contrast, past Dudear email campaigns carried the malware as attachment or used malicious URLs. pic.twitter.com/mcRyEBUmQH — Microsoft Security Intelligence (@MsftSecIntel) January 30, 2020. TA505 hacking group has been active since 2014 focusing on Retail and banking sectors.






















Let's personalize your content