DirtyMoe botnet infected 100,000+ Windows systems in H1 2021
Security Affairs
JUNE 22, 2021
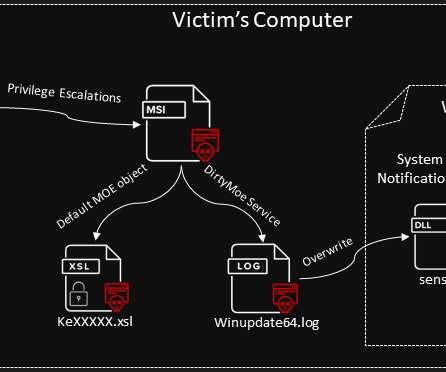
The Windows botnet has been active since late 2017, it was mainly used to mine cryptocurrency, but it was also involved in DDoS attacks in 2018. “Recently, a new infection vector that cracks Windows machines through SMB password brute force is on the rise” reads the analysis published by AVAST.




























Let's personalize your content