When Low-Tech Hacks Cause High-Impact Breaches
Krebs on Security
FEBRUARY 26, 2023
million customers, including website administrator passwords, sFTP credentials, and private SSL keys; -December 2022: Hackers gained access to and installed malware on GoDaddy’s cPanel hosting servers that “intermittently redirected random customer websites to malicious sites.”












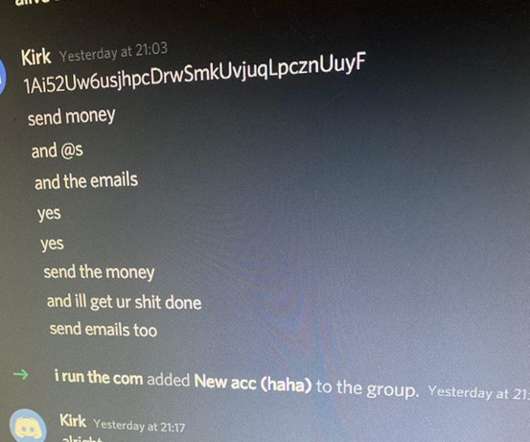












Let's personalize your content