Data Breach: Turkish legal advising company exposed over 15,000 clients
Security Affairs
FEBRUARY 26, 2021
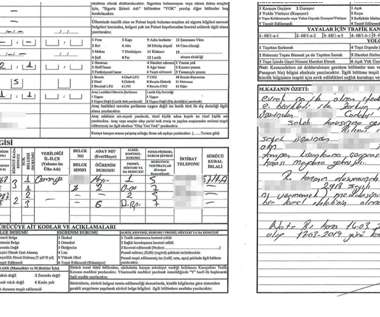
Data Breach: WizCase team uncovered a massive data leak containing private information about Turkish Citizens through a misconfigured Amazon S3 bucket. How Did the Data Breach Happen? Whose Data was Exposed and What Are the Consequences. Identity theft. How and Why We Discovered the Breach.
















Let's personalize your content