Glupteba botnet is back after Google disrupted it in December 2021
Security Affairs
DECEMBER 19, 2022
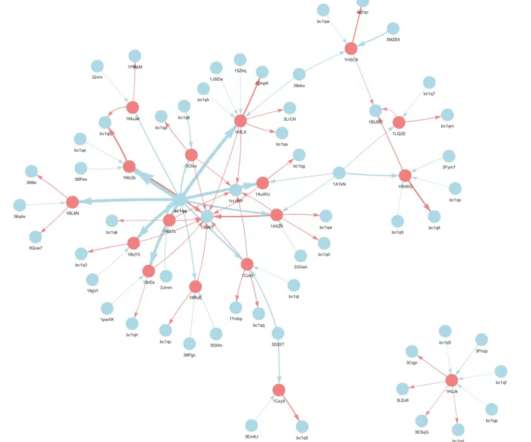
Researchers believe that at least five different merchants and exchanges were used to fund the Glupteba addresses since 2019. The experts used passive DNS records to uncover Glupteba domains and hosts and analyzed the latest set of TLS certificates used by the bot to figure out the infrastructure used by the attackers.























Let's personalize your content