How Secure Shell (SSH) Keys Work
Security Boulevard
AUGUST 5, 2022
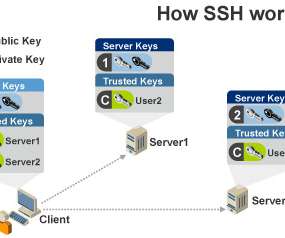
As Justin Elingwood of DigitalOcean explains , SSH encrypts data exchanged between two parties using a client-server model. That initial connection sets the stage for the server and client negotiating the encryption of the session based upon what protocols they support. It was originally published on February 5, 2019. ) .











Let's personalize your content