Microsoft: Attackers Exploiting ‘ZeroLogon’ Windows Flaw
Krebs on Security
SEPTEMBER 24, 2020
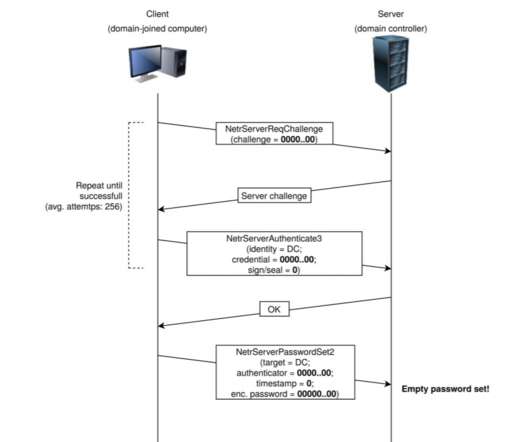
DHS’s Cybersecurity and Infrastructure Agency (CISA) said in the directive that it expected imminent exploitation of the flaw — CVE-2020-1472 and dubbed “ZeroLogon” — because exploit code which can be used to take advantage of it was circulating online.


















Let's personalize your content