Russian Cybercrime group is exploiting Zerologon flaw, Microsoft warns
Security Affairs
OCTOBER 10, 2020
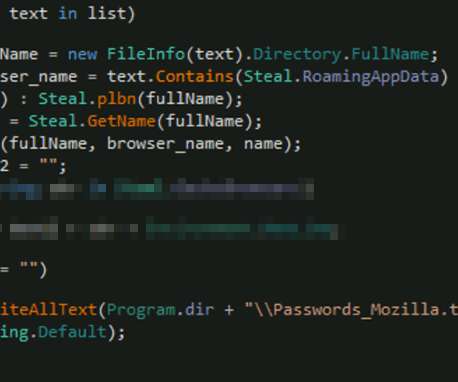
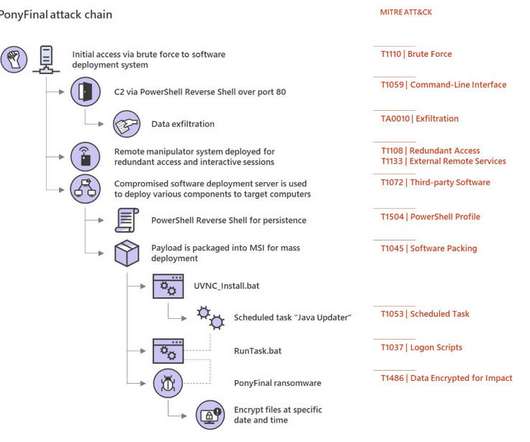
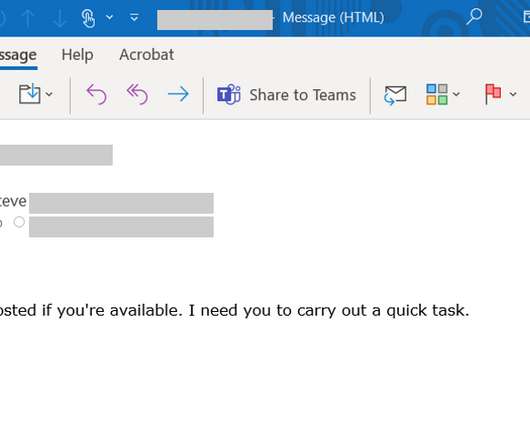
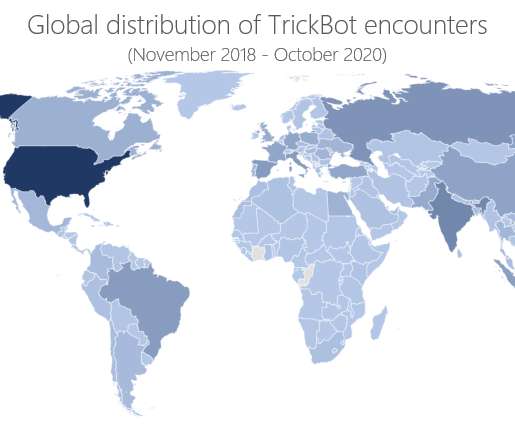
Microsoft has uncovered Zerologon attacks that were allegedly conducted by the infamous TA505 Russia-linked cybercrime group. Microsoft spotted a series of Zerologon attacks allegedly launched by the Russian cybercrime group tracked as TA505 , CHIMBORAZO and Evil Corp. states Microsoft. We strongly recommend patching.
















Let's personalize your content