Cybercrime gang FIN7 returned and was spotted delivering Clop ransomware
Security Affairs
MAY 20, 2023
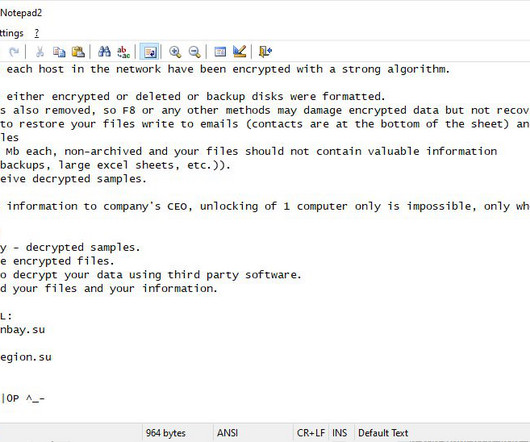
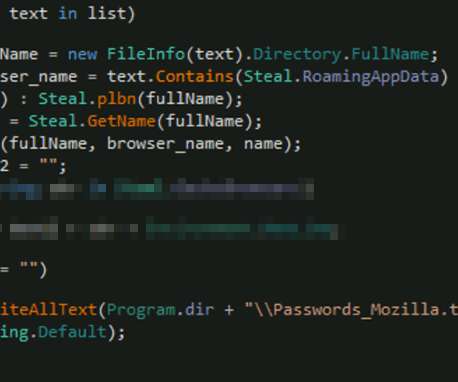
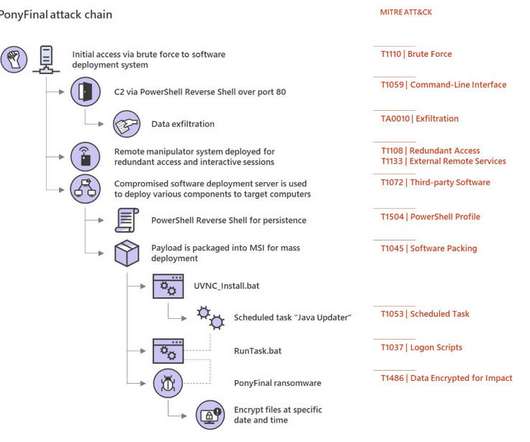
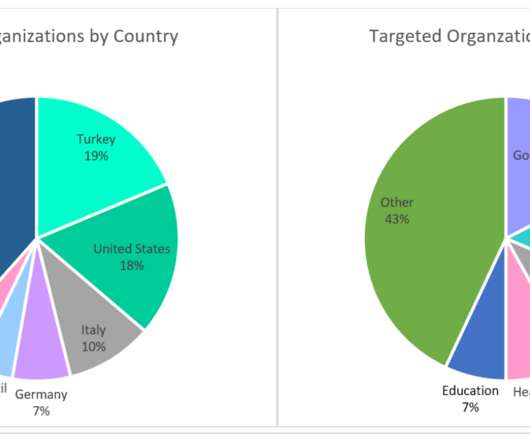
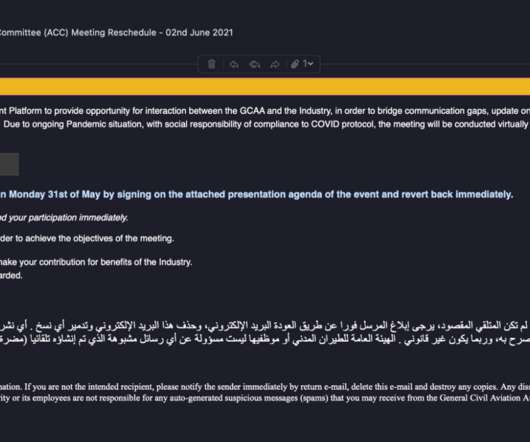
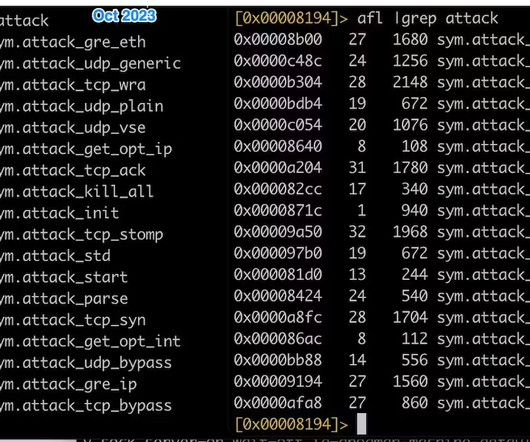
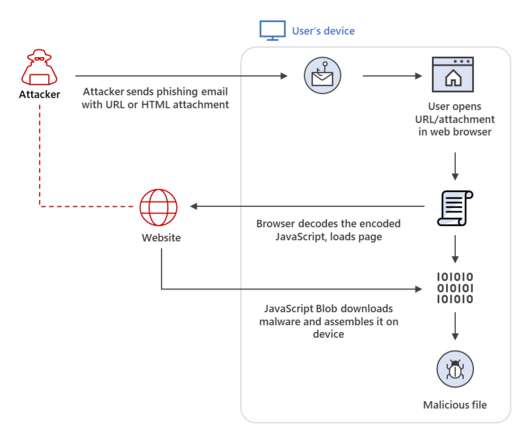
Researchers at Microsoft Security Intelligence team published a series of tweets to warn of a new wave of attacks aimed at distributing the Clop ransomware and linked it to the financially motivated cybercriminal group Sangria Tempest (ELBRUS, FIN7 ). They then use OpenSSH and Impacket to move laterally and deploy Clop ransomware.






















Let's personalize your content