Most of 2023’s Top Exploited Vulnerabilities Were Zero-Days
Schneier on Security
NOVEMBER 18, 2024
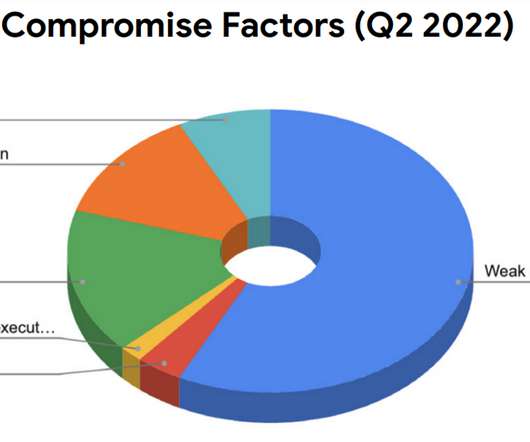
Zero-day vulnerabilities are more commonly used , according to the Five Eyes: Key Findings In 2023, malicious cyber actors exploited more zero-day vulnerabilities to compromise enterprise networks compared to 2022, allowing them to conduct cyber operations against higher-priority targets.













































Let's personalize your content