SOC 2025: Detection/Analytics
Security Boulevard
MARCH 10, 2022
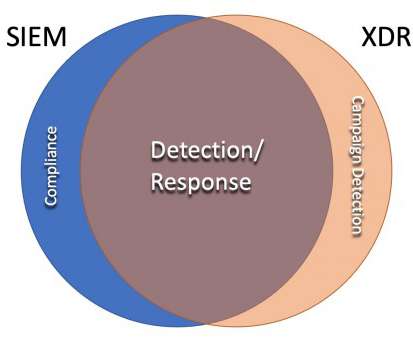
Attackers are more organized and proficient — once they have a foothold within a victim’s network, they perform extensive reconnaissance to find and destroy backups, increasing pressure to pay the ransom. You already have security monitoring technology, which you probably don’t want to (or can’t) forklift. Mike Rothman. (0)

























Let's personalize your content