Auditing the IRS: Asset Management Problems Causing Cybersecurity Risks
SecureWorld News
AUGUST 26, 2020
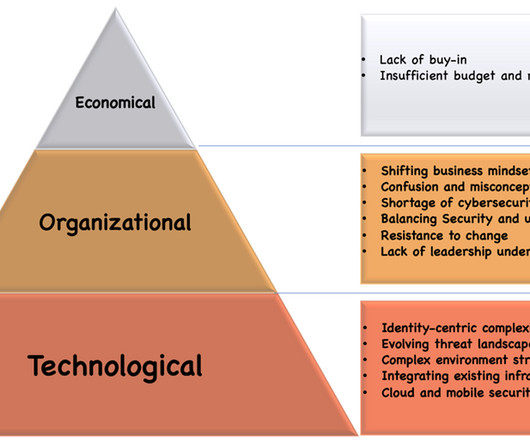
The Inspector General's report summarizes the IRS and its IT environment like this: "The reliance on legacy systems, aged hardware and software, and use of outdated programming languages poses significant risks, including increased cybersecurity threats and maintenance costs. How massive is the IRS information technology infrastructure?

















Let's personalize your content