MY TAKE: Securing the Internet of Everything: why self-healing devices are the next frontier
The Last Watchdog
FEBRUARY 10, 2025
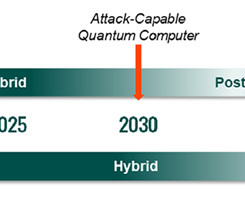
We went over how Zero Trust Architecture ( ZTA ) is gaining steam — and how it embodies a critical paradigm shift necessary to secure hyper-interconnected services. Statista estimates there will be north of 30 billion connected devices by 2030, embedded in systems as varied as pacemakers, wind turbines and smart refrigerators.


















Let's personalize your content