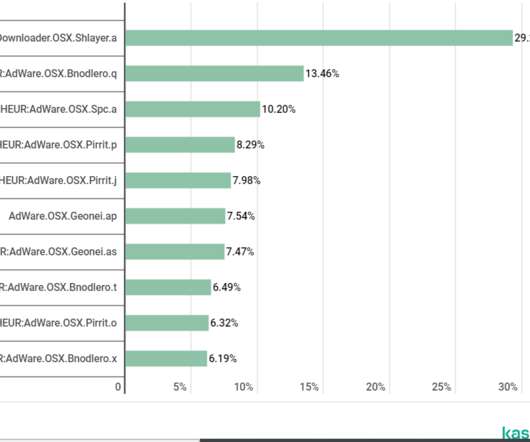
Which was the most common threat to macOS devices in 2019? Shlayer malware
Security Affairs
JANUARY 27, 2020
The malware installs Any Search bar on the targeted Mac device to deploy adware, it also intercepts and collects browser data and it is able to alter search results to deliver malicious ads. ” The malware was used to deliver multiple adware including AdWare. . Cimpli, AdWare. Bnodlero, AdWare.


















Let's personalize your content