How to Protect Your Accounts with Multi-Factor Authentication
Duo's Security Blog
OCTOBER 13, 2023
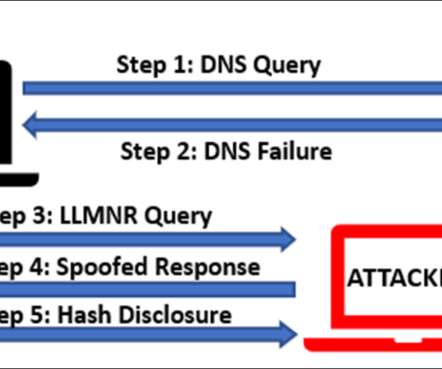
Multi-factor Authentication (MFA) protects your environment by guarding against password weaknesses with strong authentication methods. In our last blog, we discussed using strong passwords and a password manager to provide better defense at the first layer of the authentication process. Those exploits continue to this day.














































Let's personalize your content