Kaseya Left Customer Portal Vulnerable to 2015 Flaw in its Own Software
Krebs on Security
JULY 8, 2021
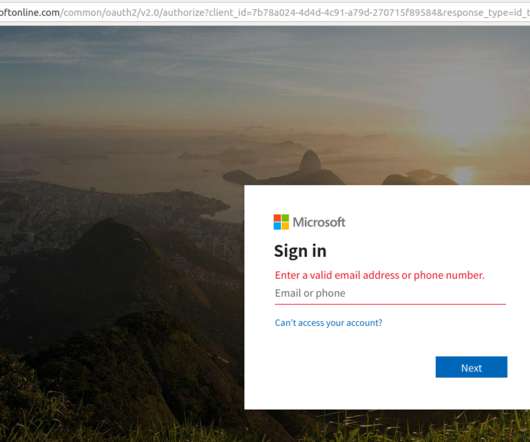
The attackers exploited a vulnerability in software from Kaseya , a Miami-based company whose products help system administrators manage large networks remotely. “It’s a patch for their own software. “This is worse because the CVE calls for an authenticated user,” Holden said.






































Let's personalize your content