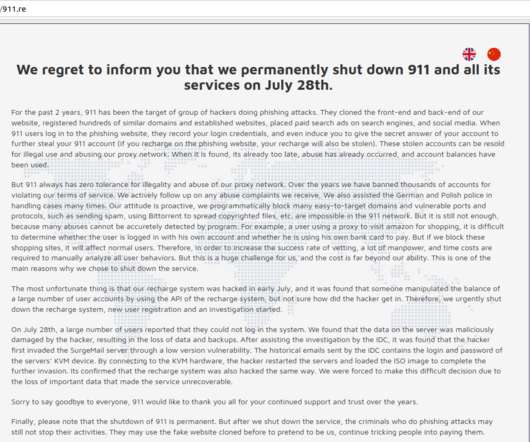
Leaked Chats Show LAPSUS$ Stole T-Mobile Source Code
Krebs on Security
APRIL 22, 2022
The logs indicate LAPSUS$ had exactly zero problems buying, stealing or sweet-talking their way into employee accounts at companies they wanted to hack. The LAPSUS$ group had a laugh at this screenshot posted by their leader, White, which shows him reading a T-Mobile news alert about their hack into Samsung.












































Let's personalize your content