Upgrading your Android device? Read this first
Malwarebytes
OCTOBER 8, 2023
Back up your data You can back up content, data, and settings from your phone to your Google Account. Select Google And then Backup. Tip: If this is your first time, turn on Backup by Google One and follow the on-screen instructions. Please keep in mind that your Google One backup can take up to 24 hours. Tap Back up now.























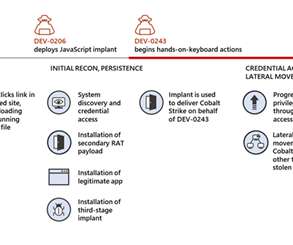




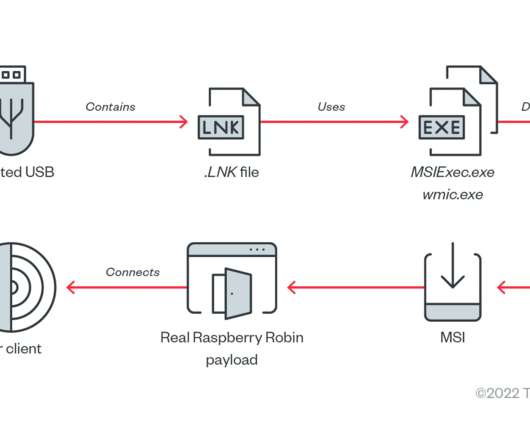
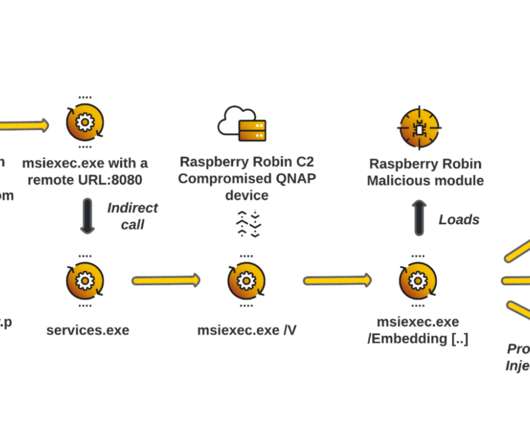




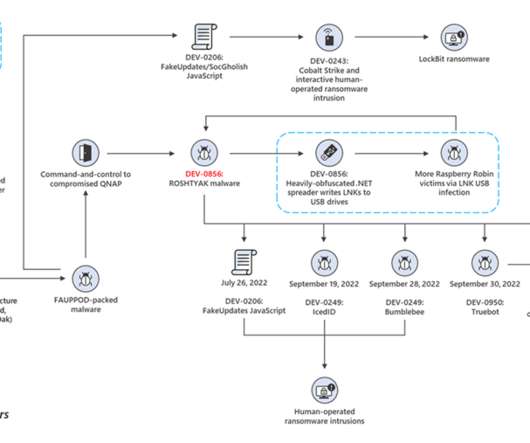













Let's personalize your content