Hackers stole millions of dollars from Uganda Central Bank
Security Affairs
NOVEMBER 30, 2024
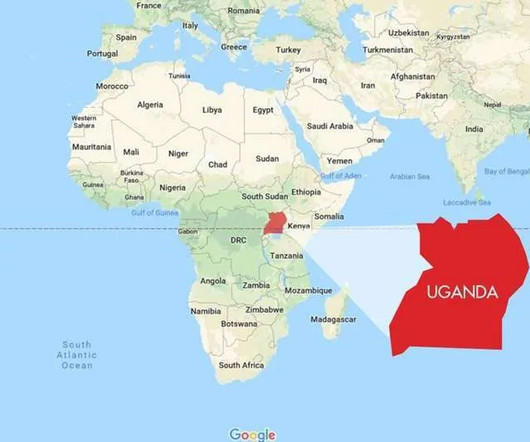
Financially-motivated threat actors hacked Uganda ‘s central bank system, government officials confirmed this week. Ugandan officials confirmed on Thursday that the national central bank suffered a security breach by financially-motivated threat actors. The Daily Monitor newspaper reported that the attackers stole 47.8








































Let's personalize your content