Mapping Penetration Testing report and vulnerability management CVEs
NopSec
MARCH 27, 2015
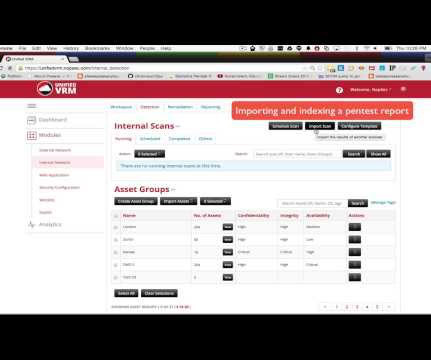
Penetration tests are point-in-time adversarial tests aimed at testing the intrusion prevention, detection, and incident response capabilities and controls of an organization. Once the pen testing report is delivered, the vulnerabilities are remediated with various degree of urgency. Thanks @mubix.

























Let's personalize your content