Google Cybersecurity Action Team Threat Horizons Report #9 Is Out!
Anton on Security
FEBRUARY 7, 2024
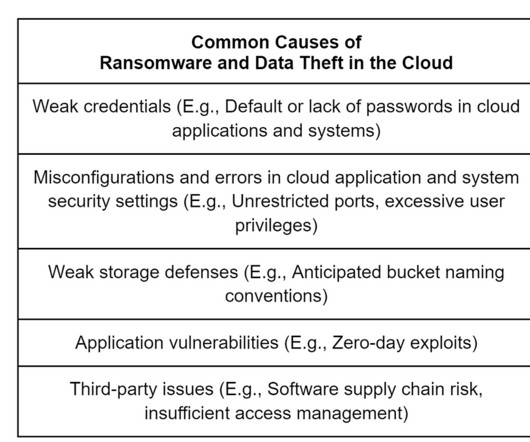
] “Given that harvesting such credentials is low-effort for a threat actor, this trend will likely continue to affect organizations that fail to meet basic standards of security. ” “ Cryptomining remained one of the principal motivations behind threat actors who abused cloud access , accounting for nearly two-thirds of observed activity.
















































Let's personalize your content