Microsoft disrupts SEABORGIUM ’s ongoing phishing operations
Security Affairs
AUGUST 15, 2022
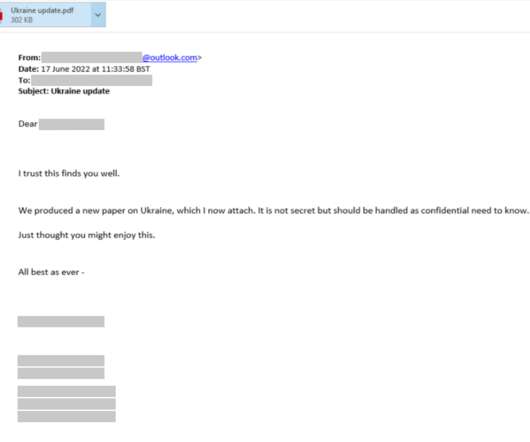
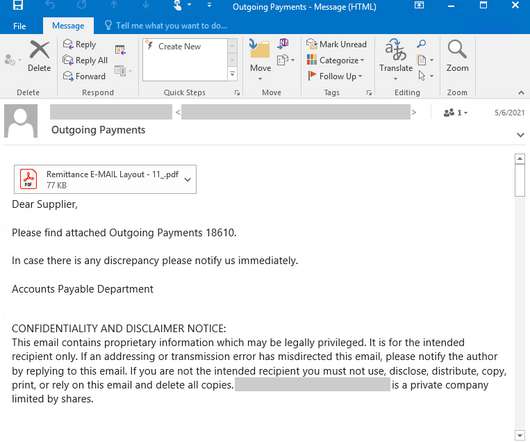
More details + TTPs in this MSTIC blog: [link] — Microsoft Security Intelligence (@MsftSecIntel) August 15, 2022. The phishing messages used PDF attachments and in some cases, they included links to file or document hosting services, or to OneDrive accounts hosting the PDF documents.












Let's personalize your content