Feds Charge Five Men in ‘Scattered Spider’ Roundup
Krebs on Security
NOVEMBER 21, 2024
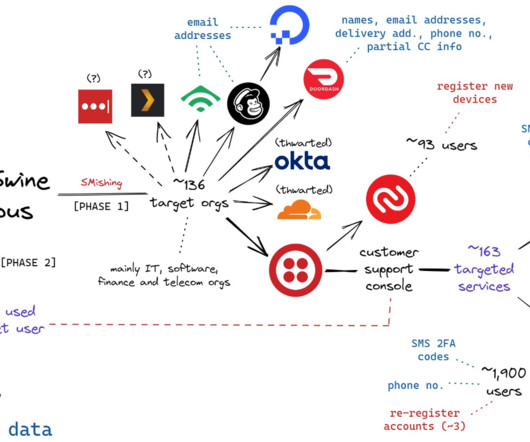
That Joeleoli moniker registered on the cybercrime forum OGusers in 2018 with the email address joelebruh@gmail.com , which also was used to register accounts at several websites for a Joel Evans from North Carolina. Click to enlarge. A Scattered Spider phishing lure sent to Twilio employees.
















































Let's personalize your content