Ukraine Nabs Suspect in 773M Password ?Megabreach?
Krebs on Security
MAY 19, 2020
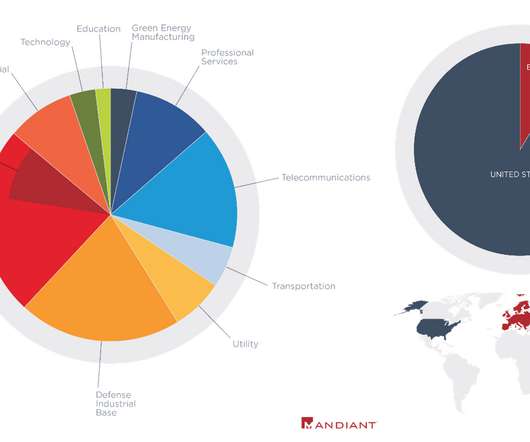
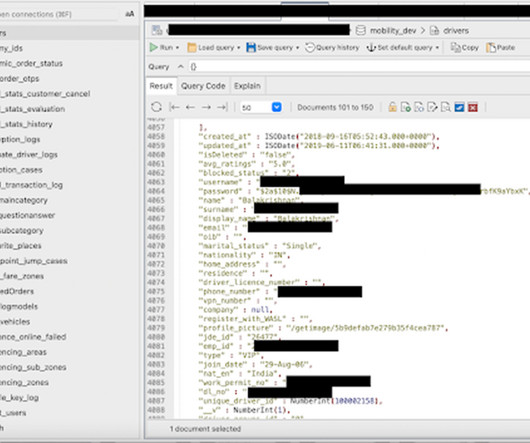
In January 2019, dozens of media outlets raised the alarm about a new “megabreach” involving the release of some 773 million stolen usernames and passwords that was breathlessly labeled “the largest collection of stolen data in history.” By far the most important passwords are those protecting our email inbox(es).














































Let's personalize your content