A Day in the Life of a Prolific Voice Phishing Crew
Krebs on Security
JANUARY 7, 2025
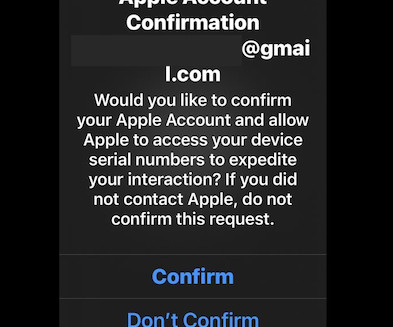
KrebsOnSecurity recently told the saga of a cryptocurrency investor named Tony who was robbed of more than $4.7 million in cryptocurrencies from Tony was verify-trezor[.]io. Federal Communications Commission (FCC), as well as those working at the cryptocurrency exchanges Coinbase and Binance. Image: Shutterstock, iHaMoo.





































Let's personalize your content