Influence Tactics in Marketing and Sales
Security Through Education
JANUARY 26, 2022
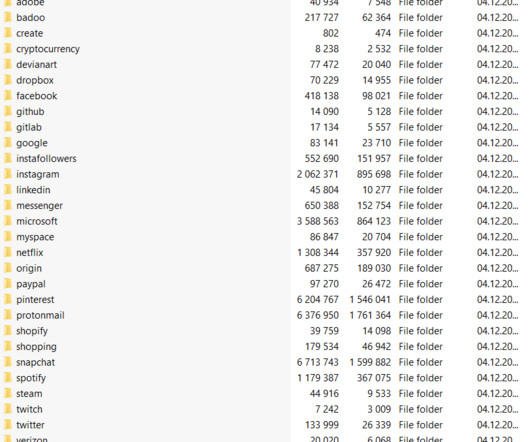
According to Rob Sanders , digital marketing expert, social media platforms supply marketers with a vast amount of data to know what content is working and what isn’t. Marketers utilize aggregate data , collected from online purchases and website visits, alongside social engineering to keep you purchasing, downloading, and revisiting.



















Let's personalize your content