State of Malware 2024: What consumers need to know
Malwarebytes
FEBRUARY 6, 2024
Sadly, there’s not a lot you can do to prevent incidents like these yourself, other than stay on top of the news and protect yourself against identity theft. This allows them to capture login credentials and even multi-factor authentication (MFA) tokens. But other threats you can do something about. This is changing.




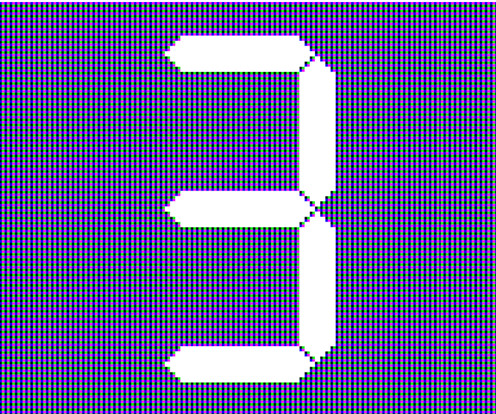









Let's personalize your content