US govt agencies released a joint alert on the Lockbit 3.0 ransomware
Security Affairs
MARCH 18, 2023
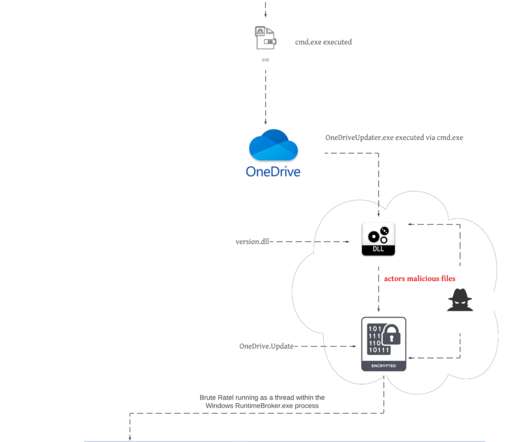
Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information Sharing & Analysis Center (MS-ISAC) released a joint advisory that provides indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) associated with the notorious LockBit 3.0



















Let's personalize your content