Avast researchers released a free BianLian ransomware decryptor for some variants of the malware
Security Affairs
JANUARY 16, 2023
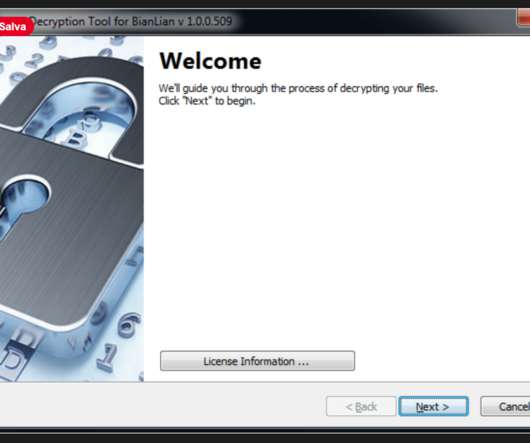
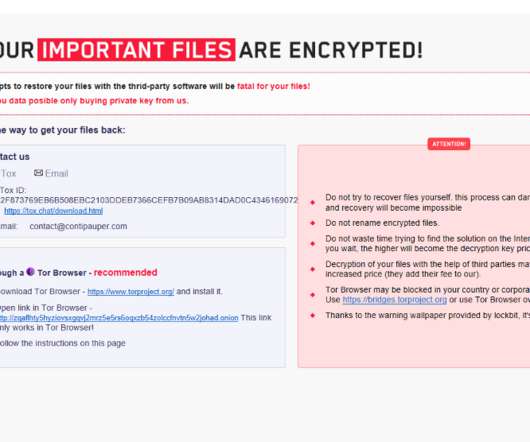
Antivirus firm Avast released a free decryptor for the BianLian ransomware family that allows victims to recover locked files. Security firm Avast has released a free decryptor for the BianLian ransomware to allow victims of the malware to recover locked files. It is also recommendable to check the virus vault of your antivirus.










































Let's personalize your content