ClamAV Bugs Expose Users to Command Injection (CVE-2024-20328) and DoS Attacks (CVE-2024-20290)
Penetration Testing
FEBRUARY 7, 2024
Recently, Cisco revealed critical vulnerabilities lurking within ClamAV, a widely used open-source antivirus engine.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Penetration Testing
FEBRUARY 7, 2024
Recently, Cisco revealed critical vulnerabilities lurking within ClamAV, a widely used open-source antivirus engine.

Penetration Testing
FEBRUARY 9, 2024
A proof-of-concept (PoC) for CVE-2024-20328, a critical vulnerability in ClamAV, a popular open-source antivirus engine, that allows arbitrary code execution, was published. It is here,... The post No Click Required: PoC Available for ClamAV Command Injection Bug (CVE-2024-20328) appeared first on Penetration Testing.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Boulevard
JANUARY 12, 2022
With a year-on-year increase of over 161% , malicious usage of cracked versions of Cobalt Strike (a legitimate penetration test tool) is skyrocketing. Developed in 2012 to give pen testers and red teams the capability to conduct hard-to-spot test attacks, Cobalt Strike is designed to be dynamic and evasive.

Hacker's King
DECEMBER 16, 2024
Phishing and Social Engineering : Phishing remains a popular attack method, leveraging emails, fake websites, and social media to deceive users into providing sensitive information. In 2023, there was a significant increase in phishing attacks, especially targeting remote workers and users in industries such as finance and healthcare.

SecureWorld News
DECEMBER 30, 2024
Antivirus solutions, monitoring systems, and endpoint detection and response (EDR) tools play a critical role in combating these threats. Social engineering techniques enable them to bypass technical security measures effectively. Social engineering techniques enable them to bypass technical security measures effectively.

eSecurity Planet
APRIL 18, 2022
Also read: Best Penetration Testing Tools. Top Open Source Penetration Testing Tools. Antivirus and EDR tools, SIEM systems (security information and event management), security vendors, software, hardware, firmware, and operating systems. What Data Do Hackers Collect? The Top Reconnaissance Tools.

Krebs on Security
MARCH 2, 2022
. – Testers: Workers in charge of testing Conti malware against security tools and obfuscating it. – Reverse Engineers: Those who can disassemble computer code, study it, find vulnerabilities or weaknesses. – Administrators: Workers tasked with setting up, tearing down servers, other attack infrastructure.

Penetration Testing
JANUARY 9, 2020
Quark Engine An Obfuscation-Neglect Android Malware Scoring System Android malware analysis engine is not a new story. Every antivirus company has its own secrets to build it. With curiosity, we develop a malware scoring... The post Quark Engine v23.11.1

Security Affairs
AUGUST 20, 2018
Today I’d like to share the following reverse engineering path since it ended up to be more complex respect what I thought. During the analysis time, only really few Antivirus (6 out of 60) were able to “detect” the sample. AntiVirus Coverage. Significative the choice to use a .reg

eSecurity Planet
MARCH 17, 2023
Encryption Product Guides Top 10 Full Disk Encryption Software Products 15 Best Encryption Software & Tools Breach and Attack Simulation (BAS) Breach and attack simulation (BAS) solutions share some similarities with vulnerability management and penetration testing solutions.

Security Affairs
JUNE 17, 2019
The file looks like a common XLS file within low Antivirus detection rate as shown in the following image (6/63). Antivirus Detection Rate. It looks like a romantic Emotet according to many Antivirus so I wont invest timing into this well-known Malware. Public Submitted Sample on Yomi. But let’s move on the analysis.

The Last Watchdog
JUNE 21, 2020
David Balaban is a computer security researcher with over 17 years of experience in malware analysis and antivirus software evaluation. David has a strong malware troubleshooting background, with the recent focus on ransomware countermeasures.

NopSec
AUGUST 2, 2017
Antivirus software is one of the oldest and the most ever present security control against malware and various types of malicious software. I have antivirus so I’m covered” used have some legitimate weight to it. Hope for the best that the target does not have an antivirus or an end point security tool! <For

Security Affairs
OCTOBER 17, 2018
Everything started from a well-crafted email targeting the right office asking for naval engine spare parts prices. The mail was quite clear, written in a great language within detailed spare parts matching the real engine parts. I do have a MD in computer engineering and a PhD on computer security from University of Bologna.

eSecurity Planet
MARCH 9, 2023
The following tools provide strong options to support vulnerability scanning and other capabilities and also offer options specifically for service providers: Deployment Options Cloud-based On-Prem Appliance Service Option Carson & SAINT Yes Linux or Windows Yes Yes RapidFire VulScan Hyper-V or VMware Virtual Appliance Hyper-V or VMware Virtual (..)

eSecurity Planet
FEBRUARY 23, 2022
57% of ICS sites do not run automatically updating antivirus protection. Network engineers use network segmentation rules to restrict sections of the network to specific users, security controls, or devices. Different IT engineers have different specialties. 84% of sites have at least one remotely accessible device.

Malwarebytes
MAY 19, 2022
These may be obtained by phishing, social engineering, insider threats, or carelessly handed data. Use antivirus solutions : Workstations require security solutions capable of dealing with exploits that require no user interaction and attacks reliant on social engineering. Valid accounts.

eSecurity Planet
DECEMBER 30, 2020
Compliance and security analysts, incident responders, engineers, and forensic investigators work together to offer uninterrupted monitoring and improved incident protection. While the latest patches for antivirus software require time-sensitive management, your SECaaS automatically covers these updates on all of your devices.

SecureWorld News
FEBRUARY 27, 2022
It was once the case that the majority of businesses could rely on a good firewall and antivirus solution. Indeed, while antivirus and firewall software do still play an important role in cybersecurity, they are not enough on their own. Using penetration testing as well as other forms of ethical hacking is a great way to do this.
Centraleyes
OCTOBER 3, 2024
Scriptable: Nmap’s scripting engine (NSE) allows users to automate tasks like vulnerability detection and malware scanning, making it highly customizable. Use Cases: Wireshark is essential for network engineers and security professionals in diagnosing network problems, detecting malicious activities, and analyzing data breaches.

eSecurity Planet
MARCH 14, 2023
Often auditing will be performed through the review of networking logs, but penetration testing and vulnerability scanning can also be used to check for proper implementation and configuration. Endpoint security : protects endpoints with antivirus, endpoint detection and response (EDR) tools, etc. for unauthorized access.

Hacker's King
OCTOBER 21, 2024
Ethical Hacking and Penetration Testing Yes, cybersecurity experts can hack your phone—but with good intentions. Ethical hackers perform what is called penetration testing or pen testing. For instance, companies might hire ethical hackers to test the security of their employees' smartphones.

SecureList
DECEMBER 14, 2020
Detecting an exploit or trojan that explicitly runs on a device is not a problem for an antivirus solution. Antivirus solutions will also recognize these files as “trusted”, so may be unable to quickly “understand” that the piece of office software is executing atypical processes initiated by malicious code.

Centraleyes
MARCH 13, 2025
Endpoint Security: Utilize firewalls, antivirus software, and intrusion detection systems to prevent unauthorized access. Schedule periodic penetration testing and vulnerability assessments to identify weaknesses before attackers do. Use these tests to refine your policies and improve your defenses.

Security Affairs
SEPTEMBER 5, 2018
One gang member – a developer – has skills of a highly experienced reverse engineer. However, in development he makes a number of errors, that are quite common for virus analysts or reverse engineers; he knows exactly how to develop software, but he does not know how to program properly.

Security Boulevard
OCTOBER 2, 2023
Phishing attackers are increasingly using social engineering techniques to personalize their attacks and target specific individuals or organizations. Social engineering - Psychological manipulation triggers emotions like fear, curiosity, or a sense of urgency that override caution.

eSecurity Planet
MARCH 22, 2023
Penetration testing and vulnerability scanning should be used to test proper implementation and configuration. Endpoint Security: Antivirus , anti-spyware , endpoint detection and response (EDR), and other controls should be deployed to secure the endpoint against compromise. and mobile (phones, tablets, etc.)

eSecurity Planet
JULY 19, 2023
The open source security tool, Nmap, originally focused on port scanning, but a robust community continues to add features and capabilities to make Nmap a formidable penetration testing tool. This article will delve into the power of Nmap, how attackers use Nmap, and alternative penetration testing (pentesting) tools.

Hacker's King
OCTOBER 10, 2024
These software solutions range from antivirus programs and firewalls to more advanced intrusion detection systems and encryption tools. Penetration Testing Penetration testing is a service where cybersecurity companies simulate real-world attacks on an organization’s network to find vulnerabilities before hackers do.

Hacker's King
OCTOBER 15, 2024
YOU MAY WANT TO READ ABOUT: Free White Rabbit Neo AI For Penetration Testing and Hacking Non-Coding Roles in Cybersecurity There are many roles within cybersecurity that focus more on strategy, risk management, and analysis, rather than on technical coding tasks.

Zigrin Security
OCTOBER 11, 2023
For a detailed threat actor description do not forget to check out our blog article about selecting between black-box, white-box, and grey-box penetration tests and also you would know which pentest you need against a specific threat actor. Regularly conduct cybersecurity training sessions to reinforce good security habits.
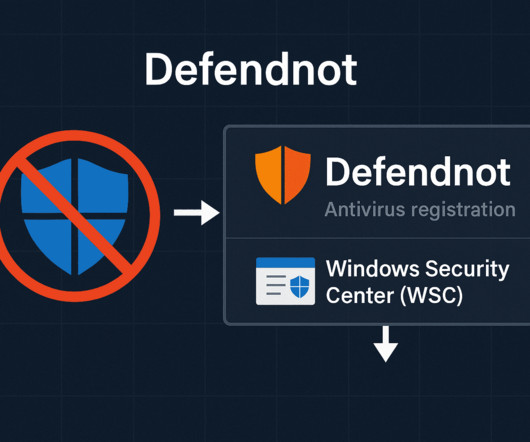
Penetration Testing
MAY 11, 2025
Security researcher Arsenii es3n1n has released a security tool named Defendnotan experimental utility that disables Windows Defender by The post Defendnot: New Tool Directly Disables Windows Defender appeared first on Daily CyberSecurity.

Responsible Cyber
JULY 13, 2024
Social Engineering Techniques Social engineering is different—it’s about manipulating people instead of hacking technology. Here are some common social engineering techniques: Phishing: Sending fake emails that look real to trick users into clicking on bad links or sharing sensitive info. What makes training effective?

eSecurity Planet
APRIL 26, 2022
Company Sector Year Status Satori DataSecOps 2021 Private BluBracket Software supply chain 2021 Private Cape Privacy Data security 2021 Private ZecOps Digital forensics 2019 Private SecurityScorecard Risk ratings 2017 Private Carbon Black Security software 2015 Acquired: VMware AVG Antivirus software 2015 Acquired: Avast. ForgePoint Capital.
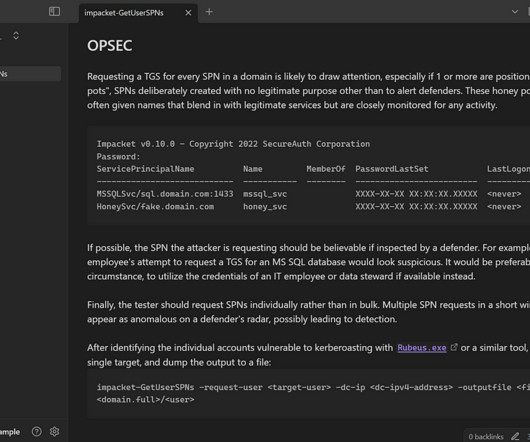
Security Boulevard
FEBRUARY 12, 2025
PEN-200: Penetration Testing Certification with Kali Linux | OffSec A Little Bit AboutMe I am an associate consultant in the offensive security consulting industry, having successfully transitioned from a career as a software engineer in information technology (IT).

SiteLock
OCTOBER 12, 2021
David Balaban is a computer security researcher with over 17 years of experience in malware analysis and antivirus software evaluation. David runs MacSecurity.net. David has a strong malware troubleshooting background, with a recent focus on ransomware countermeasures.

ForAllSecure
APRIL 26, 2023
Common Types of Cyber Attacks Common techniques that criminal hackers use to penetrate systems include social engineering, password attacks, malware, and exploitation of software vulnerabilities. Software Vulnerabilities Exploiting software vulnerabilities is one of the most common ways that hackers penetrate systems.

Security Boulevard
JANUARY 17, 2024
Antivirus Inspection Not all RBI products will prioritize this time factor. Lance has over seven years of experience in information technology with five of those specializing in Red Teaming and Penetration Testing. About Us Lance Cain is an Adversary Simulation Senior Consultant with SpecterOps.

Cytelligence
FEBRUARY 25, 2023
Phishing: Phishing is a type of social engineering attack where cybercriminals trick people into giving away sensitive information such as usernames, passwords, and credit card details. Ensure that your antivirus and anti-malware software is up to date and regularly run scans to detect any potential threats.

NetSpi Executives
APRIL 27, 2024
Ransomware, a definition Ransomware is a set of malware technologies, hacking techniques, and social engineering tactics that cybercriminals use to cause harm, breach data, and render data unusable. Do antivirus and endpoint detection and response (EDR) tools stop ransomware? Increasingly, they also threaten to leak stolen data.

SiteLock
OCTOBER 21, 2021
David Balaban is a computer security researcher with over 17 years of experience in malware analysis and antivirus software evaluation. projects that present expert opinions on contemporary information security matters, including social engineering, malware, penetration testing, threat intelligence, online privacy, and white hat hacking.

eSecurity Planet
DECEMBER 3, 2021
Russian software engineer Eugene Kaspersky’s frustration with the malware of the 80s and 90s led to the founding of antivirus and cybersecurity vendor Kaspersky Lab. Graham Cluley started as a videogame developer and antivirus programmer three decades ago before serving in senior roles at Sophos and McAfee.

ForAllSecure
FEBRUARY 8, 2023
So basically, we deliver custom penetration tests. For example, some of our tools are actually recognized by various antivirus services, not because they contain a virus, but because it's considered to be a hacking tool, which we definitely use for our pandas. Being on the good side and also on the bad side. And secure Academy.

eSecurity Planet
JANUARY 11, 2022
ai presents its solution, the NodeZero, as Autonomous Penetration Testing as a Service (APTaaS) for identifying an organization’s potential attack vectors. Also read: Antivirus vs. EPP vs. EDR: How to Secure Your Endpoints. Startup Est Headquarters Staff Funding Funding Type Horizon3 2019 San Francisco, CA 56 $38.5
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content