News alert: SpyCloud study shows gaps in EDR, antivirus — 66% of malware infections missed
The Last Watchdog
APRIL 7, 2025
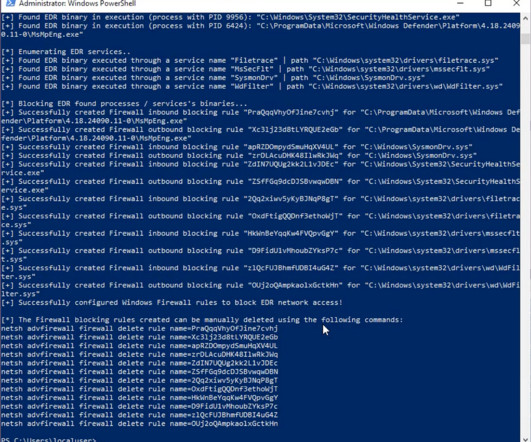
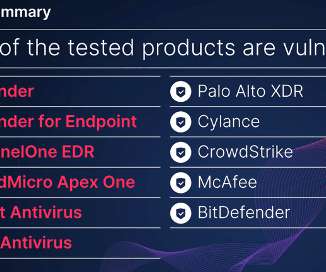
SpyClouds findings underscore that while EDR and antivirus (AV) tools are essential and block a wide range of security threats, no security solution can block 100% of attacks. The post News alert: SpyCloud study shows gaps in EDR, antivirus 66% of malware infections missed first appeared on The Last Watchdog.









































Let's personalize your content