Recent Cyber Attacks: Trends, Tactics, and Countermeasures
Hacker's King
DECEMBER 16, 2024
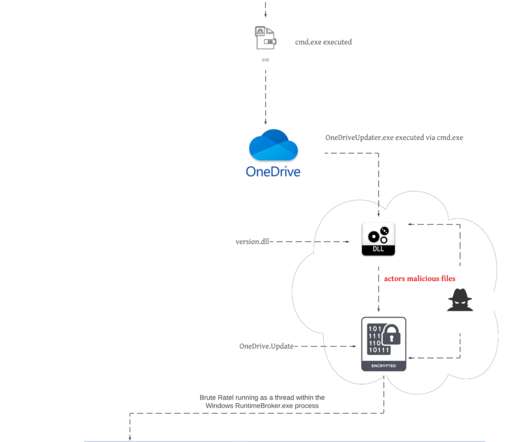
Phishing and Social Engineering : Phishing remains a popular attack method, leveraging emails, fake websites, and social media to deceive users into providing sensitive information. In 2023, there was a significant increase in phishing attacks, especially targeting remote workers and users in industries such as finance and healthcare.











































Let's personalize your content