Pixel 6: Setting a new standard for mobile security
Google Security
OCTOBER 27, 2021
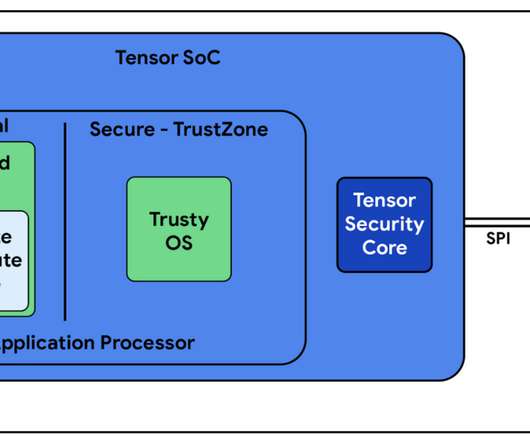
TrustZone is a key part of our security architecture for general secure processing, but the security improvements included in Google Tensor go beyond TrustZone. Capping off this combined hardware and software security system, is the Titan Backup Architecture, which gives your Pixel a secure foot in the cloud.































Let's personalize your content